The world’s 1st
Quantum Safe
Zero-trust Networking
Quantum-resistant data in transit and rest.
Out-of-the-box advanced zero trust security.
Converge networking and security from day zero.
On-demand create and manage networks tailored to your needs.
Empower your business to stay agile, secure, and ready for any challenge.

What Makes Gopher Sec Special
Built on Open Standards
A two-phase handshake protocol is designed to make Gopher end-to-end encrypted and quantum-resistant. Simply, quantum key is computed during phase 1, and Noise key is negotiated in phase 2 but with quantum key as the pre-shared key, which end up having dual encryption, i.e. classical and quantum encryption.
Gopher Sec is built on the Noise Protocol, the same protocol that WireGuard and other networking products (e.g. Bitcoin Lightning Network, WhatsApp, etc.) are built on.
To withstand attacks by large quantum computers, Crystal-Kyber protocol is used to implement the key encapsulation mechanism (KEM), whose security is based on the hardness of solving the learning-with-errors (LWE) problem over module lattices.
Device Clone-Proof
- Zero trust SIM.
- Timing based key reshuffle.
- Biometric and crypto fingerprints.
- Contextual factors lock-in.
Access Control
- Enforce policies at every layer.
- Identity-and-context aware access control.
- Policy, attribute and role based access control.
Service and Event Mesh
Quickly and easily create mesh networks for services and events.
Policies are injected into network and application layers of service and event mesh to enforce just-in-time authorization.
Attributes can be user-defined to achieve dynamic access control.
.png)
Security At Every Layer
Comprehensive protection, safeguarding your data and operations at every step. Trust in a solution where security isn't an afterthought—it's built into the very fabric of our technology.
Advanced Zero Trust
Every access request is verified, protecting your network with continuous authentication and dynamic access controls
Quantum-resistant End-to-End Encryption
Stay ahead of threats with protection free from advanced man-in-the-middle attacks and resilient against emerging quantum threats
Policy Enforcement
Enforce policy from layer 3 all the way to 7, ensuring your network remains secure and compliant at all time
Traffic Inspection
Monitor and analyze data flows in real-time, detecting threats and anomalies before they can cause harm
Network Micro-segmentation
Isolates critical assets and prevent lateral data breach using micro-segmented networks
Context-aware Authentication
Adapt to user behavior and environmental factors, providing robust, personalized protection.
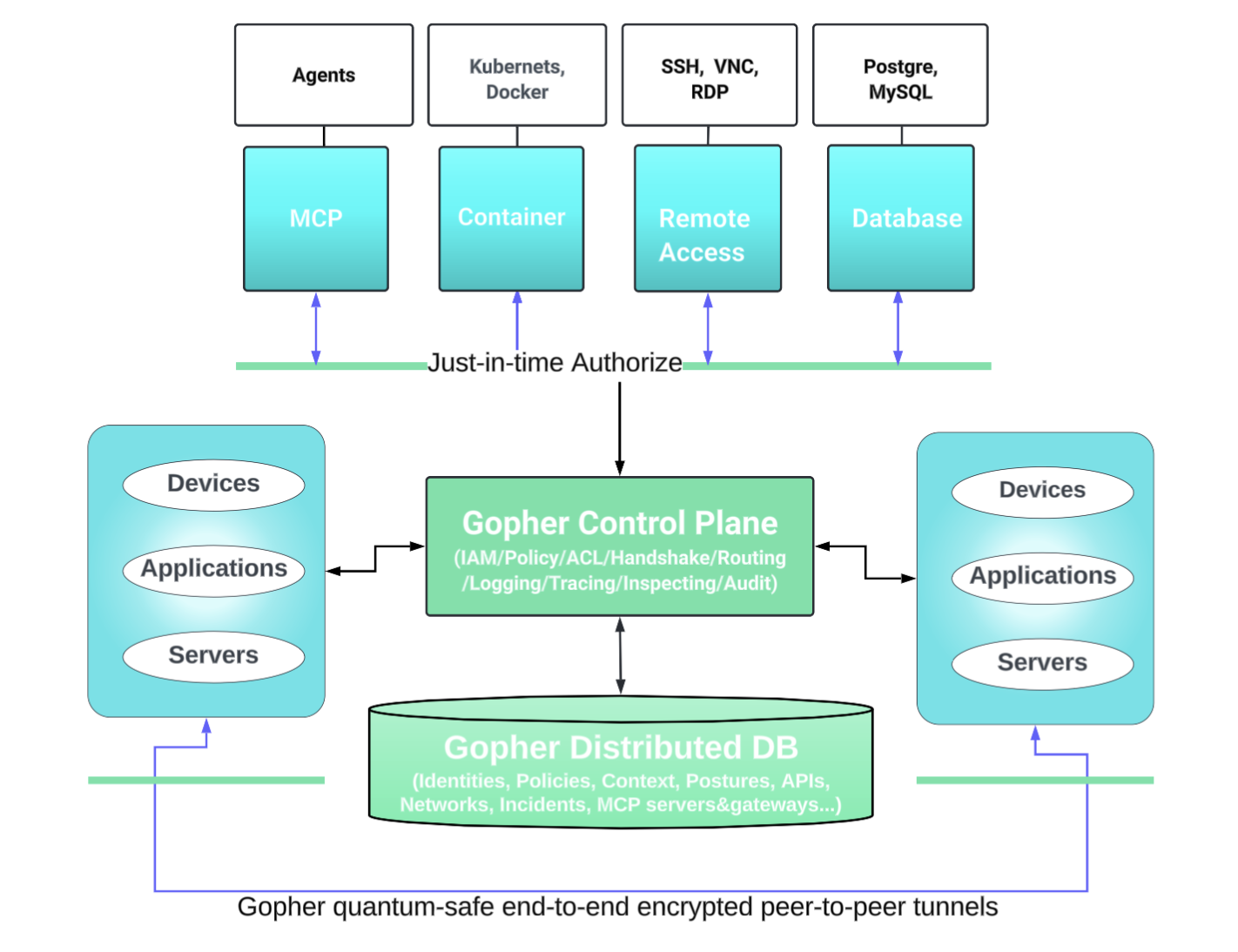
How Gopher Sec Works
Admins use Gopher Dashboard to create networks and configure security policies.
Employees are invited to join networks and sign in with correct identities and credentials.
Just-in-time policies checks are triggered for every request to authorize access.
Quantum-safe end-to-end encrypted peer-to-peer tunnels are created to let users access resources.