Gopher JITA: Secure and Simple Just-in-Time Access for Enterprise Environments

TL;DR
- Gopher JITA offers an innovative and secure solution for just-in-time access, providing businesses with a seamless way to grant temporary, limited access to critical resources. This approach ensures minimal attack surfaces while adhering to advanced security principles like Zero Trust, micro-segmentation, and context-aware authentication.
Summary
Just-in-time access (JITA) is a security practice that grants users temporary, limited access to resources only when needed. This approach minimizes attack surfaces and reduces the risks associated with excessive and persistent privileges. Gopher JITA offers an innovative, secure, and user-friendly way to implement just-in-time access with built-in Zero Trust, micro-segmentation, and context-aware security. This blog explores how Gopher JITA can transform your access management by comparing it to traditional methods and highlighting its benefits. Another good read is Enhance Security with Just-in-Time Access: Best Practices to Minimize Risks.
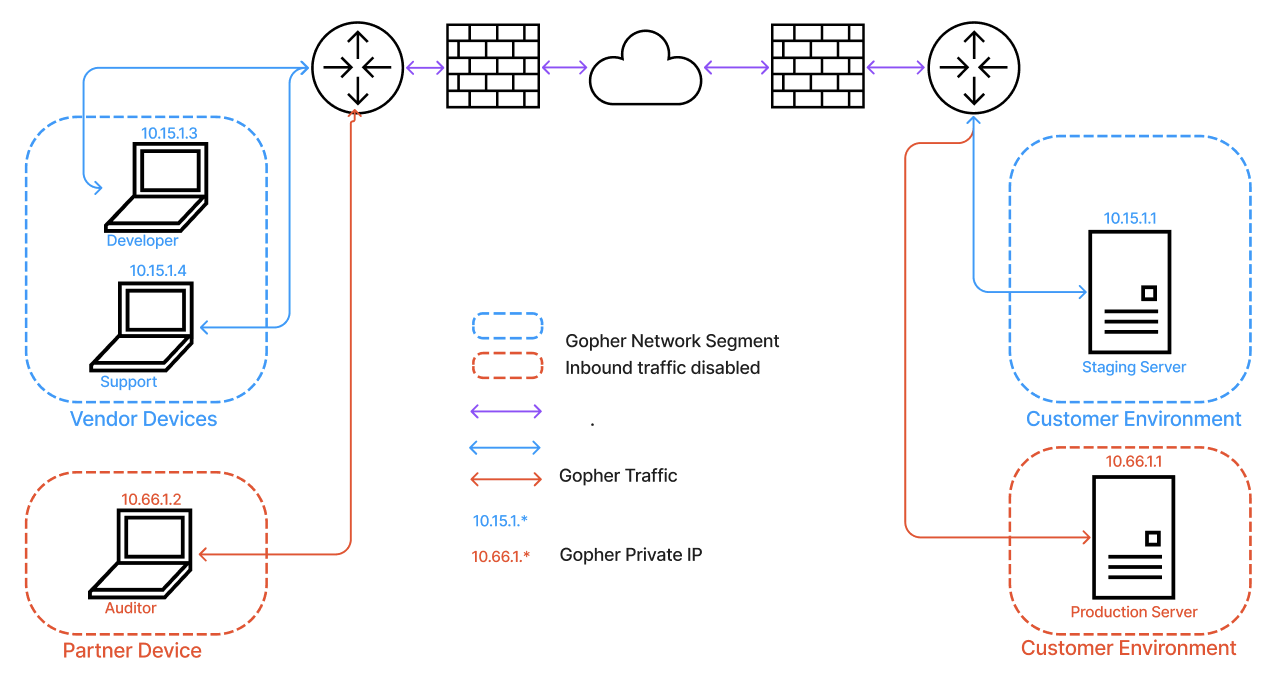
Gopher JITA: Just-In-Time Access Customer's Staging and Production Environments Securely, Powered by Gopher Attribute-based Access Control and Quantum-safe Micro-segmentation
What is Just-in-Time Access?
Just-in-time access is a method that provides users, vendors, and partners temporary, time-bound access to specific resources only when required. Once the task is complete, the access is revoked. This is particularly useful in reducing risks tied to long-standing, unchecked permissions that attackers can exploit.
Why Do You Need Just-in-Time Access for Better Security?
The evolving threat landscape demands heightened security measures, especially in environments involving remote work, cloud infrastructure, hybrid setups, and AI adoption. Persistent access can leave networks vulnerable to exploitation, especially across multi-environments like testing, staging, and production. JITA reduces the window of opportunity for attackers by granting access only when absolutely necessary and revoking it afterward.
Vulnerabilities Without JITA:
Long-standing access can result in stolen credentials being exploited without detection.
Insider threats are more likely when staff members retain access to critical systems they no longer need.
Poor management of permissions can lead to excessive access rights, increasing the risk of lateral attacks within the network.
Traditional Approach to Just-in-Time Access
Traditional Approach:
Traditionally, just-in-time access is enforced by manual intervention, such as issuing time-bound credentials or configuring temporary roles. However, this method is often inefficient, lacks scalability, and can result in delays when urgent access is needed.
Gopher JITA:
Gopher JITA automates this process by providing a seamless and secure way to manage access, integrating zero trust principles and leveraging Gopher's advanced technologies.
Customer Value:
Gopher JITA saves time and reduces risks associated with manual access management, ensuring quick, secure, and time-bound access while adhering to zero trust principles.
Gopher JITA Benefits Compared to Traditional Approaches
1. Vendor Staff Access on Demand
Traditional Approach:
Vendor staff often need access to testing or staging environments, but granting them persistent access can expose sensitive data and resources to risks. This is traditionally done through VPN or static user credentials, which remain active for extended periods.
Gopher JITA:
With Gopher JITA, vendors can be granted on-demand, time-bound access to testing and staging environments. Once the work is completed, access is automatically revoked, preventing overexposure.
Customer Value:
This approach minimizes the attack surface by ensuring access is available only when necessary and reduces the chance of sensitive information being compromised.
2. Partner and Auditor Access to Production
Traditional Approach:
Partners, such as auditors, are typically given extensive access to production environments, which may pose a security risk if not managed effectively. Access may also remain active beyond the required period.
Gopher JITA:
Gopher JITA allows partners and auditors to gain timed access to production environments securely. Access is limited to the duration of their tasks, preventing any prolonged exposure.
Customer Value:
This ensures sensitive production data is secure, while auditors can still perform their tasks efficiently without risking long-term exposure.
3. Role and Group-Based Access Control
Traditional Approach:
Traditional access control often relies on predefined roles, which can lead to excessive access rights, especially in rapidly changing environments.
Gopher JITA:
Gopher JITA uses role and group-based access control to ensure that only authorized personnel have access to the resources they need, and no more.
Customer Value:
This principle of least privilege helps limit potential threats, as users are only granted permissions they require to perform their specific tasks.
4. Attribute-Based Access Control (ABAC)
Traditional Approach:
Traditional access control methods often fail to meet the dynamic needs of modern businesses, as they do not incorporate factors like identity, time, or location.
Gopher JITA:
Gopher JITA enforces attribute-based access control (ABAC), allowing administrators to set access parameters based on factors like identity, time, location, and more.
Customer Value:
This ensures that access controls are flexible and adapt to the specific needs of each situation, ensuring tighter security across various business contexts.
5. Micro-Segmentation
Traditional Approach:
In traditional networks, the lack of micro-segmentation often leads to broad access across environments, increasing the risk of lateral movement during an attack.
Gopher JITA:
Using micro-segmentation, Gopher JITA isolates vendor, partner, and customer environments, limiting any threat spread across network perimeters.
Customer Value:
This significantly reduces the risk of lateral movement within a network, protecting sensitive systems from potential breaches.
6. Context-Aware Authentication
Traditional Approach:
Traditional methods often lack the depth to verify contextual factors like location, IP, or device fingerprinting, allowing attackers to bypass standard authentication.
Gopher JITA:
Gopher JITA enforces context-aware authentication, incorporating elements like IP addresses, locations, and device fingerprints, ensuring that only legitimate devices can access the system.
Customer Value:
This drastically reduces the chance of unauthorized devices gaining access, adding an extra layer of security to your network.
7. Quantum-Resistant Encryption
Traditional Approach:
Encryption mechanisms in traditional setups may be vulnerable to future quantum computing attacks, putting data at risk.
Gopher JITA:
Gopher JITA provides quantum-resistant end-to-end encryption, ensuring that even the most advanced man-in-the-middle attacks are thwarted.
Customer Value:
This future-proofs your organization’s encryption strategies, protecting against emerging threats posed by quantum computing.
8. No Public IP Required
Traditional Approach:
Public IPs are typically used to connect remote users, but they expose networks to a variety of external threats.
Gopher JITA:
With Gopher JITA, no public IPs are required; connections use Gopher private IPs, which are protected behind several security layers.
Customer Value:
By eliminating public IPs, you remove a significant attack vector, reducing the overall risk of external threats.
9. Built-In Zero Trust and SASE Capabilities
Traditional Approach:
Traditional just-in-time access controls lack the built-in Zero Trust and Secure Access Service Edge (SASE) capabilities needed to minimize insider and external threats.
Gopher JITA:
Gopher JITA integrates both Zero Trust and SASE, ensuring that all access is continuously verified and that the entire network remains secure from internal and external threats.
Customer Value:
This enhances the overall security posture of your organization, preventing both insider attacks and external breaches.
10. Inbound Traffic Disabled
Traditional Approach:
Traditional just-in-time access mechanisms often leave open inbound ports, exposing networks to external threats.
Gopher JITA:
Gopher JITA disables inbound traffic, protecting your test, staging, and production environments from external threats.
Customer Value:
This makes your environments bulletproof against external attacks, securing sensitive data from outside threats.
Inheriting Gopher’s Out-of-the-Box Security From Layer-3/4 to 7
Enforcing Tunnel Match at Layer-3/4
Gopher JITA: Enforces secure tunnels between authenticated endpoints at Layer-3 and Layer-4.
Customer Value: Reduces unauthorized access and strengthens overall network security.
Enforcing Policy Match at Layer-3/4
Gopher JITA: Ensures all network traffic complies with organizational policies.
Customer Value: Enhances compliance and minimizes policy gaps.
Enforcing Network Segment Match at Layer-3/4
Gopher JITA: Implements micro-segmentation for secure isolation of network segments.
Customer Value: Protects against lateral data breaches.
Traffic Observability at Layer-3/4
Gopher JITA: Offers complete traffic observability for real-time monitoring and detection.
Customer Value: Detects anomalies early, ensuring performance and compliance.
Contextual Factors Match at Layer-7
Gopher JITA: Enforces access based on real-time contextual factors (identity, location, device).
Customer Value: Ensures secure, context-aware access control.
Policy Match at Layer-7
Gopher JITA: Strictly enforces policies for sensitive resource access.
Customer Value: Prevents unauthorized access to critical resources.
Traffic Inspection at Layer-7
Gopher JITA: Conducts deep traffic inspection at the application layer.
Customer Value: Protects against modern, application-level threats.
Enabling Service Mesh at Layer-7
Gopher JITA: Seamlessly integrates with service mesh for secure microservices communication.
Customer Value: Enhances security and performance in cloud-native environments.
Quantum-Resistant End-to-End Encryption
Gopher JITA: Provides quantum-resistant encryption to safeguard data from future threats.
Customer Value: Future-proofs your network against evolving quantum threats.
Pluggable Framework to Extend Data Plane
Gopher JITA: Offers a pluggable framework for extending security features.
Customer Value: Adapts to evolving security needs without system overhauls.
Disabling Inbound Traffic to Prevent External Threats
Gopher JITA: Disables inbound traffic, allowing only authorized Gopher tunnels.
Customer Value: Bulletproofs the network from external threats like DDoS and unauthorized access.
Conclusion
Gopher JITA delivers a comprehensive and secure solution for managing just-in-time access, allowing businesses to maintain control over who can access their systems, when, and for how long. Its innovative features, including micro-segmentation, Zero Trust security, and context-aware authentication, offer unparalleled protection for modern businesses.
Final Thoughts and Recommendation
In today's remote work and hybrid environments, securing just-in-time access has become paramount. Gopher JITA provides a future-proof solution with its dynamic, scalable, and secure approach. We highly recommend adopting Gopher JITA to protect your network while providing seamless, secure access to users and partners when they need it most.





