Gopher Private: Redefining Enterprise Private Networks with Superior Security and Performance

TL;DR
- Gopher Private delivers unmatched security, flexibility, and performance for enterprise private networks. Its integration of Zero Trust Network Access (ZTNA), Secure Access Service Edge (SASE), and peer-to-peer mesh networking makes it an ideal solution for modern cloud and hybrid infrastructures.
Summary
In today's complex enterprise environment, securing private networks is essential to maintain data integrity and operational continuity. Traditional private network technologies like VPNs, MPLS, and leased lines are becoming less effective in meeting the needs of modern cloud and hybrid infrastructures. Gopher Private introduces a revolutionary, software-driven approach to enterprise private networking, bringing together Zero Trust Network Access (ZTNA), Secure Access Service Edge (SASE), and peer-to-peer mesh networking to deliver unparalleled security and flexibility. This blog explores the benefits of Gopher Private, how it compares to traditional methods, and why it’s a game-changer for enterprise security. Some other good blogs are Gopher Router: Simplifying Private Network Security with Agentless Zero Trust Solution and Enhance Enterprise Security: The Essential Role of Private Networks in Cloud and Hybrid Environments.
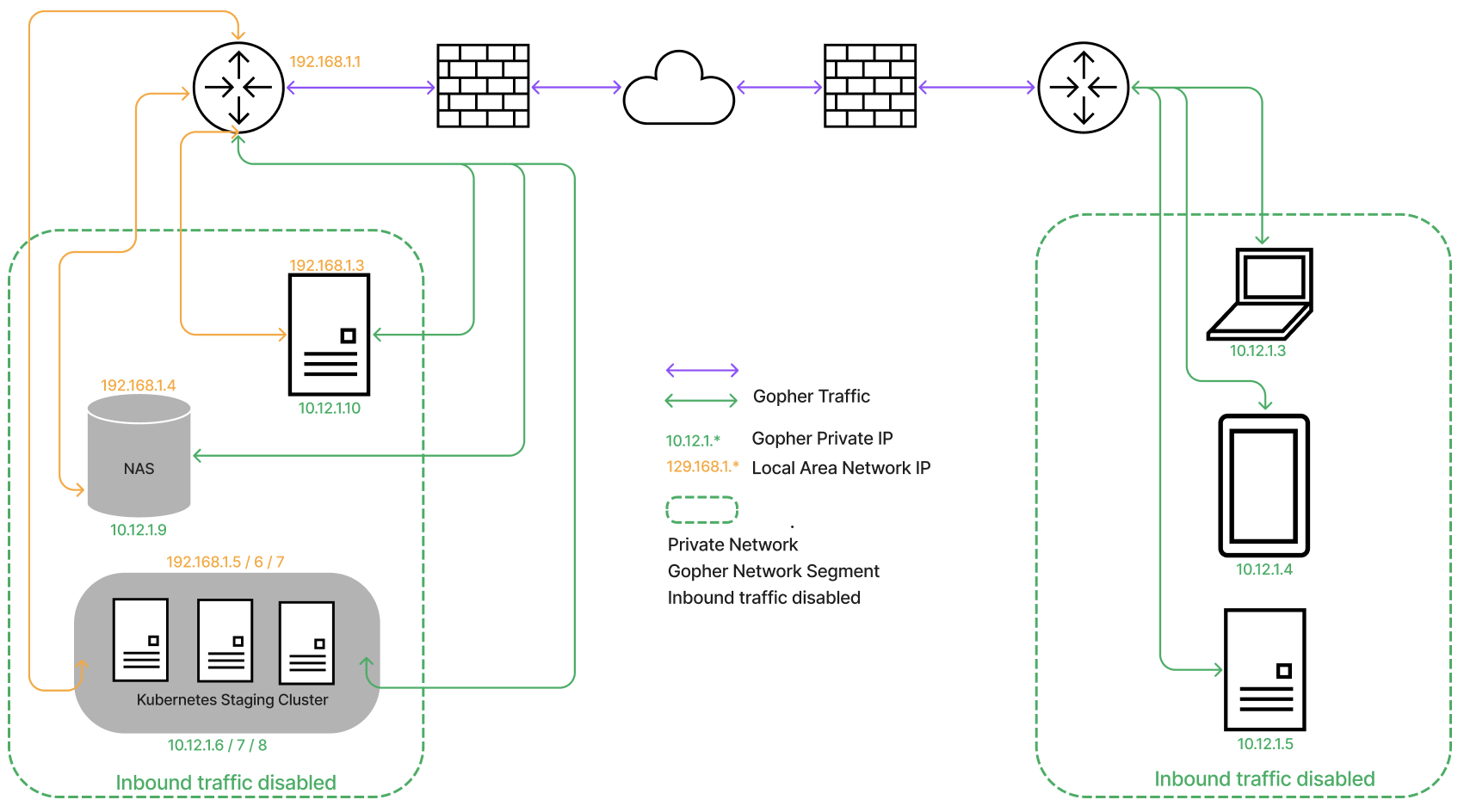
Gopher Private: Secure Enterprise Private Network Using Gopher Private IP and Quantum-safe Micro-segmentation
What is an Enterprise Private Network?
An Enterprise Private Network enables organizations to securely connect various users, devices, and locations to access corporate resources without relying on public networks. Traditionally, these private networks were built using technologies like VPNs, MPLS, leased lines, and SD-WAN to ensure secure communication between remote sites, branch offices, and cloud services. However, as enterprises move to cloud-based and hybrid models, traditional private networks are increasingly proving to be rigid, costly, and complex.
Why Do You Need Enterprise Private Network?
Enterprise private networks are crucial for securing internal communication, protecting sensitive data, and maintaining operational efficiency. However, traditional methods face growing vulnerabilities in the context of cloud adoption, remote work, and AI-driven applications. Some of these vulnerabilities include:
Limited scalability: Traditional private networks struggle to adapt to dynamic environments and scale on-demand.
Security gaps: Without Zero Trust principles, traditional networks can expose organizations to unauthorized access.
Complex management: VPNs and MPLS require intricate configuration, making them difficult to manage and scale efficiently.
Traditional Private Network Approaches
Traditional private networks rely on various technologies:
Virtual Private Networks (VPNs): VPNs use tunneling protocols to securely connect remote users to private enterprise networks over the internet. VPNs can be complex to configure and may introduce latency due to centralized points of connectivity.
Multi-Protocol Label Switching (MPLS): MPLS is a high-performance, secure WAN solution that connects geographically dispersed sites via dedicated circuits. MPLS is often expensive and slow to deploy.
Leased Lines/Private Circuits: These provide physical point-to-point connectivity between locations but are costly and lack flexibility.
VPC (Virtual Private Cloud): VPCs isolate cloud-based workloads from public networks but often rely on VPNs for connectivity to on-premises resources.
SD-WAN: SD-WAN offers flexibility by routing traffic over a mix of internet and MPLS links, but it can be complex to configure.
While these traditional approaches have been effective in the past, they are increasingly challenged by the demands of cloud-native architectures, remote work, and multi-cloud deployments.
Traditional vs. Gopher Private Networks
Complex Setup and Management vs. Simple Configuration
Traditional Networks: VPNs, MPLS, and SD-WAN typically involve complex configuration and maintenance, requiring expert knowledge. VPN endpoints must be configured manually, and MPLS often depends on ISPs for deployment, causing delays.
Gopher Private: Simplifies the entire process with a graphic user interface that minimizes manual configuration tasks. Admins can deploy and manage networks without needing expert-level knowledge, and Gopher Private provides Ansible-based automation for large-scale deployments.
Customer Value: Simplified setup reduces operational overhead and improves efficiency. Automated tools allow for quick network scaling without the complexity.
High Costs vs. Low Cost
Traditional Networks: MPLS and leased lines are expensive, especially when scaling across multiple locations. High costs and long contracts are common.
Gopher Private: Operates at a much lower cost by utilizing free internet bandwidth with peer-to-peer connectivity and NAT traversal capabilities, eliminating the need for costly infrastructure.
Customer Value: Significant cost savings by using public internet for secure communication without sacrificing security.
High Latency vs. Low Latency
Traditional Networks: VPNs and MPLS links often introduce latency due to centralized routing, resulting in performance degradation for real-time applications.
Gopher Private: Utilizes peer-to-peer networking to bypass centralized proxies, minimizing latency and improving performance for latency-sensitive applications like VoIP and video conferencing.
Customer Value: Low-latency connections ensure high performance, especially for real-time applications, improving the user experience.
Scaling Limitations vs. Horizontal Scalability
Traditional Networks: VPNs and MPLS struggle to scale dynamically, especially in cloud-native environments where applications need to scale elastically.
Gopher Private: Scales horizontally due to its peer-to-peer mesh networking, ensuring there’s no single point of failure and enabling seamless connectivity across cloud, on-premises, and hybrid environments.
Customer Value: Dynamic scalability ensures that businesses can grow without hitting network bottlenecks, improving agility in cloud-native applications.
Limited Support for Multi-Cloud vs. Environment-Agnostic Connectivity
Traditional Networks: MPLS and VPNs are not designed to support multi-cloud or hybrid environments seamlessly. Integrating multiple cloud environments often results in siloed networks that are hard to manage.
Gopher Private: Provides environment-agnostic connectivity, enabling seamless communication between multi-cloud, hybrid, and on-premises environments using mesh networking.
Customer Value: Flexibility to connect diverse environments without additional complexity, making it ideal for cloud-native and multi-cloud deployments.
Lack of Granular Access Control vs. Granular Policy Control
Traditional Networks: VPNs often allow broad access, exposing the entire network to potential security breaches.
Gopher Private: Implements Zero Trust principles with granular policy control at both the application and user levels. This ensures that only authorized users or devices can access specific resources.
Customer Value: Enhanced security with granular access control prevents unauthorized access, reducing security risks.
Security Concerns vs. ZTNA and Quantum-Resistant Encryption
Traditional Networks: VPNs and MPLS often lack advanced security features such as Zero Trust and end-to-end encryption, leaving security gaps.
Gopher Private: Delivers Zero Trust Network Access (ZTNA) and quantum-resistant end-to-end encryption to ensure that all communication remains secure and continuously authenticated.
Customer Value: Continuous authentication and advanced encryption ensure the highest level of security, protecting against emerging threats.
Lack of Application Awareness vs. Full Application Awareness
Traditional Networks: MPLS and VPNs don’t prioritize traffic based on application needs, leading to performance issues for critical workloads.
Gopher Private: Uses Envoy Proxy to enable full application awareness, supporting advanced traffic routing, Layer-7 inspection, and application-level load balancing.
Customer Value: Better performance and security by optimizing network traffic for critical applications.
Lack of Zero Trust Implementation vs. Zero Trust from Day One
Traditional Networks: Legacy solutions rely on perimeter-based security, trusting devices after the initial connection.
Gopher Private: Implements Zero Trust from day one, with continuous verification of identity, policies, and contextual factors.
Customer Value: Continuous verification ensures that only authorized users and devices can access critical resources, improving security.
Slow Provisioning vs. On-Demand Security and Networking
Traditional Networks: MPLS provisioning can take weeks, and VPNs often involve manual processes for configuration.
Gopher Private: Offers on-demand provisioning of software-defined network segments with advanced Zero Trust capabilities, reducing deployment times to minutes.
Customer Value: Speed of deployment and on-demand capabilities allow businesses to adapt quickly to changing network needs.
Siloed Management vs. Unified Networking
Traditional Networks: Managing different network types (VPNs, MPLS, cloud-native) can be challenging, often requiring separate management systems.
Gopher Private: Provides unified networking and security management through a central dashboard, connecting all environments seamlessly.
Customer Value: Simplified network management reduces operational complexity and improves visibility across the entire network.
Operational Complexity vs. Simplified Operations
Traditional Networks: Configuring and managing VPN topologies, routing, encryption, and authentication policies in traditional networks requires specialized skills and can be time-consuming.
Gopher Private: Gopher Private offers simplified operations with a central dashboard, making it easy to manage routing, IP filters, and policy controls. Key distribution simplifies node-to-node access management.
Customer Value: Simplified management allows teams to focus on core business operations rather than complex network configurations, reducing the need for specialized skills.
Limited Elasticity and Dynamic Adjustments vs. On-Demand Change and Adaptability
Traditional Networks: MPLS and VPNs are rigid and don’t dynamically adjust to changing traffic loads or network demands. Scaling typically involves costly bandwidth upgrades or manual adjustments.
Gopher Private: Gopher Private offers peer-to-peer mesh networking that dynamically adjusts to changing environments. It supports on-demand networking, ZTNA, and SASE capabilities, making it adaptable to fluctuating network demands.
Customer Value: Elastic, dynamic scalability ensures that networks can quickly adapt to changing business requirements without costly or time-consuming upgrades.
Inheriting Gopher’s Out-of-the-Box Security from Layer-3/4 to Layer-7
Enforcing Tunnel Match at Layer-3/4
Gopher Private ensures that only legitimate and secure tunnels are established by enforcing tunnel matches at both the network (Layer-3) and transport (Layer-4) layers. All data passing through the network is tightly controlled and validated, a critical feature that is often absent in legacy proxies.
Customer Value: This reduces the risk of unauthorized access and data breaches, providing a secure network environment by preventing illegitimate traffic from entering the system.
Enforcing Policy Match at Layer-3/4
By enforcing policy matches at Layer-3 and Layer-4, Gopher Private ensures that all network traffic adheres to predefined security rules. This capability is lacking in many traditional proxies, which may lead to security gaps or non-compliance.
Customer Value: This helps businesses maintain strict compliance with organizational security policies, ensuring that only authorized traffic flows through the network.
Enforcing Network Segment Match at Layer-3/4
Gopher Private enables micro-segmentation at Layer-3 and Layer-4, ensuring that each network segment is isolated and secured. This prevents unauthorized users or devices from accessing other parts of the network, reducing lateral movement within the network.
Customer Value: Protects against lateral data breaches by containing threats to specific network segments, thereby enhancing overall network security.
Traffic Observability at Layer-3/4
Gopher Private provides comprehensive traffic observability at both Layer-3 and Layer-4. This allows organizations to monitor network traffic in real-time, detect anomalies, optimize performance, and ensure compliance with security policies.
Customer Value: Complete visibility into network activity allows for proactive detection of suspicious behavior, reducing potential threats and ensuring a more secure and well-monitored network.
Contextual Factors Match at Layer-7
At Layer-7 (application layer), Gopher Private enforces contextual factors, such as user identity, device status, and location, ensuring that only legitimate requests are processed. This level of context-aware authentication is often missing in traditional proxies.
Customer Value: By considering contextual information, Gopher Private reduces the risk of unauthorized access, strengthening the security posture of the network.
Policy Match at Layer-7
Gopher Private also enforces policy matches at Layer-7, allowing it to restrict access based on detailed, application-level criteria. This ensures that only authorized users and requests reach sensitive resources, unlike legacy proxies, which lack this granular control.
Customer Value: Enhanced control over network resources improves data protection, reducing the risk of data leaks and breaches while ensuring compliance with security policies.
Traffic Inspection at Layer-7
Gopher Private performs deep packet inspection at Layer-7, analyzing all application-level data to identify and block potential threats. Legacy proxies often struggle with sophisticated modern attacks, which Gopher Private can detect and mitigate.
Customer Value: By detecting and blocking malicious activity at the application layer, Gopher Private ensures that modern threats, such as ransomware and malware, are identified and neutralized before they cause harm.
Enabling Service Mesh at Layer-7
Gopher Private supports service mesh functionality at Layer-7, enabling secure and dynamic service-to-service communication between microservices. This capability is vital for modern cloud-native applications and is often missing in traditional network architectures.
Customer Value: This improves both application performance and security by ensuring that services can communicate seamlessly and securely in dynamic environments.
Quantum-Resistant End-to-End Encryption
Gopher Private offers quantum-resistant end-to-end encryption, safeguarding sensitive data from emerging quantum computing threats. This level of security far exceeds what legacy proxies can offer.
Customer Value: By future-proofing network security with quantum-resistant encryption, Gopher Private ensures that critical data remains secure in the face of new and evolving threats.
Pluggable Framework to Extend Data Plane
Gopher Private’s pluggable framework allows organizations to extend the data plane with new features and capabilities as needed, ensuring that the network evolves alongside business requirements. In contrast, legacy proxies are often rigid and difficult to upgrade.
Customer Value: This adaptability allows businesses to keep up with evolving security needs without requiring costly overhauls or replacements of existing infrastructure.
Disabling Inbound Traffic to Prevent External Threats
Gopher Private can disable inbound traffic entirely, permitting only authorized Gopher tunnels with NAT traversal capabilities to communicate. This effectively prevents unauthorized traffic from accessing the network, a critical capability often missing in legacy proxies.
Customer Value: By restricting inbound traffic, Gopher Private offers enhanced protection from external threats, significantly reducing the attack surface and improving overall network security.
Conclusion
Gopher Private offers a next-generation solution for building secure, scalable, and efficient private networks. By integrating Zero Trust principles, quantum-resistant encryption, and peer-to-peer mesh networking, Gopher Private simplifies operations while improving security and performance.
Final Thoughts and Recommendation
Traditional private networks like VPNs and MPLS can no longer meet the needs of modern enterprises. Gopher Private offers a revolutionary approach to private networking that is built for the cloud, hybrid environments, and beyond. Its low-cost, scalable, and secure architecture makes it an essential tool for any organization looking to future-proof its network infrastructure. We highly recommend Gopher Private for businesses that need a flexible, secure, and high-performance private network solution.